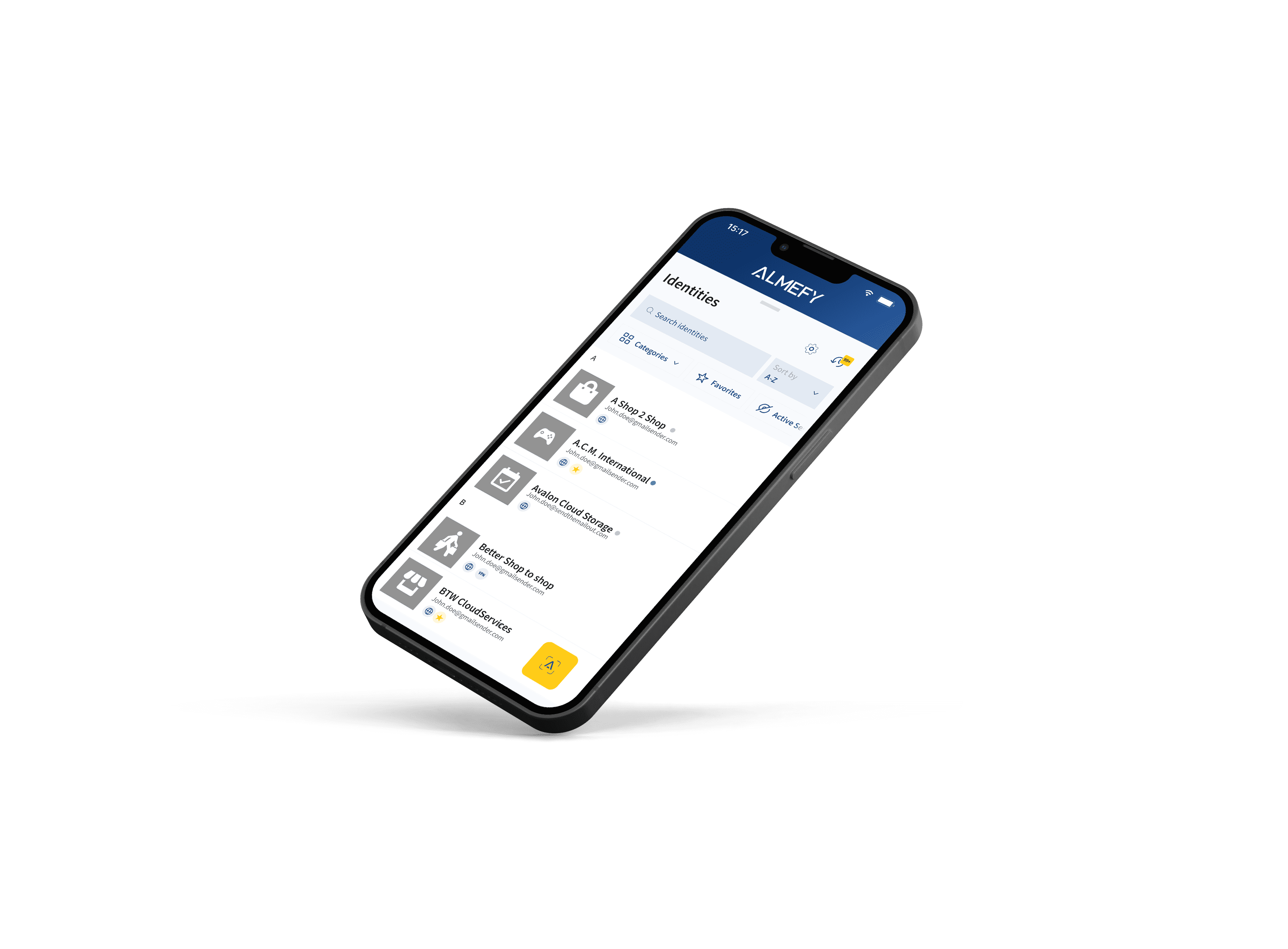
Secure Scan to login
The easiest and fastest login without passwords

Password free login
100% Secure
GDPR compliant
Made in Germany
We all know the hustle of defining and maintaining what we perceive as secure passwords. Reality is, almost no password is secure and to maintain them is a nightmare. Specially if you want to follow all the rules which cyber security experts recommend when it comes to secure passwords. And in addition, as save as it might get, phishing attacks and passwords leaks are part of our reality. Almefy has set out to solve this problem for you: All Logins Made Easy For You.
Utilizing identity based encryption (IBE) to securely login users through Two-Factor Authentication by just scanning the QR code on the login page using the Almefy App.
No password needed! Just scan to login.